Developers Beware - Rising Web3 Job Scam & HiveApp Malware!
Insights into ongoing Web3 job scam and Hive malware targeting developers
The plot
On November 30, 2024, I was approached by the COO of a company called metify.tech on X (Twitter). He wanted to discuss potential collaboration on some of his projects with me due to my experience. After checked their website, I found it to be acceptable for a start-up. He also shared projects documents that seemed legitimate, but I didn't yet have full picture of what they were really up to as I knew little about Web3 technology.
Curious, I expressed my interested in learning more. Little did I know, this was the moment I became their target. The COO asked for my Telegram username and added me to a Telegram group named "discussion #27". My instincts kicked in; I rarely used Telegram, and something felt off - specially when recruiter use Telegram with oddly named channel.
In the group, all high-ranking C-level officials of the company (CEO, CTO, CMO and rest of their team) were present. They asked about my experience, which seemed normal. I told them I had over 8 years of experience building cloud infrastructure and shared my website and LinkedIn profile.
Laying the net
The conversation continued when another person asked which project I would be interested in. I mentioned that I could assist with infrastructure and backend-related work. The CTO then asked - how long will it take to delivery this project: Advanced Caching System Development. I replied - it would take three to four months.
What happened next felt like a well-planned scam designed to make it seem like they were genuinely hiring. The COO instructed me to schedule a meeting with their HR team through Calendly, so I did.
Meet the team on HiveSpace
I booked a meeting for that same evening at 8:45 PM. However, when it was time for the meeting, I noticed something strange: there was no link provided for a video call — only a mention of Telegram.
Confused, I reached out in the group to ask where to join. The COO replied - I was late, I should show respect since the team had already joined and was waiting for me. However, I had arrived 5 minutes before the scheduled meeting.
This sudden change in tone surprised me and raised suspicion. He then sent me a link to join the meeting on a platform called HiveSpace.
The site resembled a Miro clone and felt odd platform for an interview call; it made me wonder why they didn't use common platforms like Zoom or Google Meet or even Telegram.
At this point, I knew something was up. I registered as they requested with their invite link and created an account on HiveSpace using fake info.
Meanwhile, they pressured me in the group to hurry up as the team was waiting. I informed them I had never used this app before and needed some time to set it up.
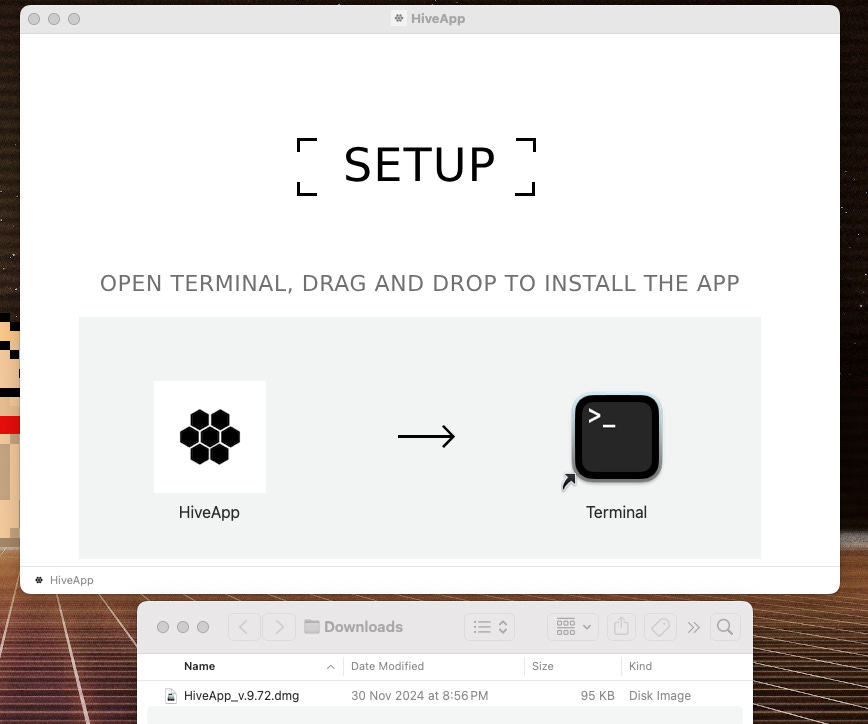
Upon registration, it immediately downloaded a client installer called HiveApp_v.9.72.dmg. It asked me to run commands in Terminal — a strange request for installing an app on Mac.
I halted the installation process and told them it wasn't working for me. They immediately suggested trying another device; when I said I don't have another device, they went quiet for a bit and said, I was taking too much time.
At this point, it seemed they were getting frustrated with me and likely realized that I wasn't falling for their scam.
Soon after, I was removed from their "discussion #27" group - something I forgot to screenshot - and their COO sent me a DM saying - "the team waited too long," and suggested to reschedule when I was free, and disappeared since without further reply.
What's inside the Hive?
Feeling stunned by what had just happened, I became curious to investigate the HiveApp installer. I launched a ephemeral Kali Linux VM using OrbStack to sandbox the malware.
The installer was named HiveApp.file and turned out to be a bash script with a random variable names consisting of base64 encoded values.
The script decodes the base64 values and executes them with inline bash command. I learned that Base64 was simple obfuscation technique often used by malware.
The installer disk image (DMG) contained other files that the installer script would use, primarily the .HiveApp binary, which is likely the actual malware.
I copied the obfuscated script to the /tmp directory in the Kali VM and modified the last command to only echo the malware's decoded content.
Since the script was using base64 with -D flag, which only worked on macOS, I replaced it with the lowercase -d flag to work on Kali Linux.
The installer script utilized Apple scripts (osascript) to copy the binary payload named .HiveApp. It then sets the executable bit on it and runs.
As I'm not a malware expert, I'm unsure how it would function; perhaps some malware experts can reverse engineer the binary.
My hunch is that the malware would connect back to Control and Command (C&C) server to download additional malware payloads.
Reporting time
I wasted no time reporting all the relevant sites to Google phishing page, Microsoft unsafe site, Cloudflare abuse report and GitHub abuse report.
Metify.tech - The project website.
HiveSpace.net - The site hosting the malware.
HiveSpaceAI/HiveSpace - GitHub repository claiming to be open-source.
Upon further investigation, it turned out all the team members had fake names impersonating real persons; here and here; every team member listed on the site was impersonated.
I've reported all fake handles on X; but as of now, they have not yet been taken down.
Protect yourself
Reflecting on this experience, I'm grateful for the security measures I've put in place on my Mac since day one— tools like Ransomwhere for detecting encryption attempts, LuLu for network filtering, and other security tools from Objective See project created by Patrick Wardle which have become Mac essential in protecting against such sophisticated threats.
For Windows users, installing antivirus (AV) and endpoint security solutions from Sophos or CrowdStrike is crucial for additional layer of protection.
Additional, for Windows users, I'd recommend installing GlassWire - a firewall and network monitor tool. This tool will notify you if new executable attempts to make network connections so you can block then if necessary or whitelist if it's known executable such as Google chrome, etc.
When in doubt about the legitimacy of a website, ask Perplexity to summarize its findings.
Raise awareness
After further research, I discovered that same threat actors have previously used other websites to carry out the same attacks, such as jaborcall.org, mefion.io and now metify.tech. It is likely that this site will be taken down soon, and they will start fresh with a new domain.
It's very important that we make a collaborative effort to report such websites. Otherwise, more people fall victim to these scams, and their operations will continue for a longer period.
Recently, these scam tend to targeted Web3 developer all over the world and are also on GitHub, using GitHub to carry out their attacks.
Sometimes the scam is obvious to spot, and sometimes it is not. Regardless, the modus operandi has remained the same: it involves a Web3 company hiring individuals to work on their project.
The purpose of writing this detailed investigative article is to raise awareness of the active, ongoing targeted malware attacks in the wild and to provide guidance on how to identify and protect yourself against them. Stay safe!